
Secure Remote Access for the Teleworker Accessing the Cloud
31st March 2020
Most companies are now in the process of rapidly enabling teleworking, telelearning, and remote productivity solutions to maintain business and operational continuity. But their goal is to also enable those remote access services in a way that does not introduce unjustified operational overhead. And at the same time, they need to maintain required levels of security to meet the existing business and operational model. This can be a complicated process in the best of times, let alone when expediency is so critical.
To complicate the process further, organizations need to provide remote users with more than just a secure connection back to the core network or datacenter resources they are used to be remotely connecting to. An increasing number of applications are also being hosted in the cloud, and rather than backhauling those applications through the core network, organisations need to consider providing secure remote connectivity directly to those applications. Direct connectivity will not only reduce the load on the network, but also improve overall user experience, especially for high-bandwidth or latency-sensitive applications.
But whether an organisation already has a remote access solution in place, or is the process of building or expanding one, it quickly becomes clear that a sudden increase in demand for remote access to applications inevitably reveals new traffic patterns that will need to be addressed, both in terms of performance and security. This is especially apparent for applications that are typically not accessed remotely (for example, from user groups that typically work from the office). These new discoveries heighten the need for a remote access solution that offers a consistent security posture across data locations globally, whether to cloud or on-premise data-centers, combined with the high performance and flexibility designed to scale to meet heightened demand.
One Security Solution for All Deployment Scenarios
Deploying large-scale VPN solutions for remote users is a thoughtful process. Beyond enabling simple access, things such as segmenting users based on role, security profile, and the content and resources they require are first-order tasks. Teams also need to identify users that require special access to resources.
Which employees are power users, such as system administrators, IT support technicians, and emergency personnel who require a higher level of access to corporate resources and the ability to operate in multiple, parallel IT environments? What about workers that process extremely sensitive and confidential information or require advanced access to confidential corporate resources, such as administrators with privileged system access, support technicians, key partners aligned to the continuity plan, emergency personnel, and executive management? And what about those users that require site-based access?
These considerations require thinking about the entire network architecture, from cloud to on-premise to endpoint. Fortinet addresses these and similar requirements by providing a flexible operating system that is consistent across form factors – whether deployed in the cloud, on-premise, or in a power user’s home office – and whose management can be centralised for policy orchestration, VPN templating, and user segmentation.
Enabling a Multi-Pronged Security Approach
Fortinet customers that deploy FortiGate solutions in the cloud, on-premise, or at remote locations are able to take advantage of its single pane of glass management, enabling the control and orchestration of multiple firewalls across locations to establish and maintain consistent security and user experience. Fortinet understands that business performance largely depends on user productivity, access to content and applications, at any location, at any time. With remote access and the ability to manage performance across locations using Secure SD-WAN as a core capability the Fortinet Security Fabric securely provides flexible options for mobile and fixed access to cloud resources at massive scale.
When deployed in AWS, for example, the FortiGate VM NGFW acting as a secure VPN gateway is able to support up-to 20Gbps of IPSec VPN traffic across Internet of Direct Connect links connecting datacenters and clouds, and tens of thousands of SSL-VPN and IPSec VPN sessions connected with FortiClient or other VPN client. This flexibility helps customers meet their remote access needs without any need to redesign networks or security policies as well as manage SLAs for traffic across locations. In those cases where the FortiGate-VM is running on a smaller compute instance, customers can scale up and launch a larger solution using the same configurations to increase capacity with minimal downtime. And they can increase their use of any Cloud based application or service whether on AWS, Azure, GCP or Oracle Cloud combined with FortiGate based SSL-VPN or IPSec VPN to gain finer visibility & control over which type of user gets access to different applications.
For such customers, it becomes possible to visualize and secure increased traffic demand in two areas:
- Because more remote access users will need to access more applications hosted in the cloud, more VPN Connections will need to be terminated both on-premise and, in the cloud, (1 in the following diagram). As a result, there will also be heightened requirements for SSL-VPN and IPSec session establishment actions with IKE v1/v2 and SSL key negotiation speeds.
- There will also be more site-to-site VPN traffic as more user’s access applications that are potentially hosted across on-premise and in the cloud (2 in the following diagram), which in turn increases traffic volume across application functions and modules. While this pattern, and its resulting decryption and encryption performance requirements would quickly overtax most NGFWs, FortiGate solutions are up to the test.
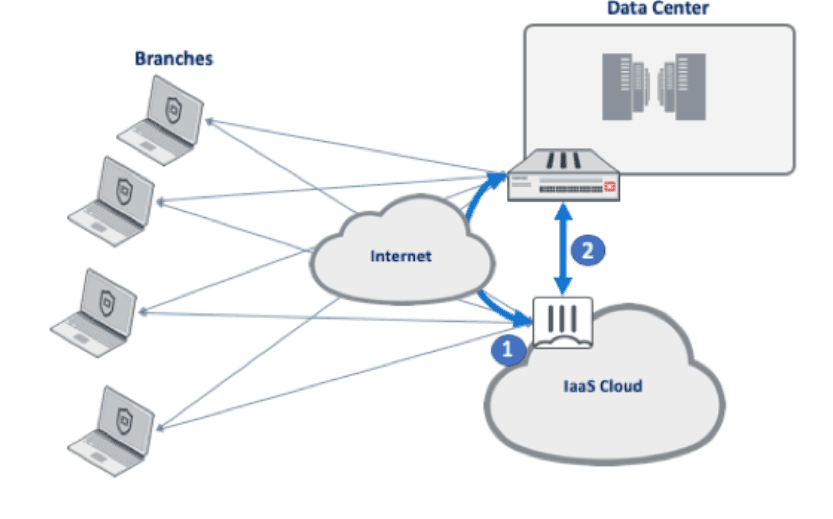
Advantages of a Unified Security Approach for Remote Access
Of course, such increased traffic demands create more stress on existing infrastructure performance and functionality are pushed to their limits. In such situations, excess performance headroom is much appreciated. At the same time, customers who have implemented Fortinet’s best-of-breed datacenter edge security solutions, along with their public cloud-based security services hub solutions, can enjoy the flexibility benefits these solutions have to offer, especially as they are able to function as a single, integrated security system.
Following are some of the leading considerations when addressing increased remote access demands:
Scale-Up vs. Scale-Out: For large-scale VPN, especially since VPN is a very stateful communications technology, new challenges are introduced when designed as a scale-out capability. The ability to implement Scale-Up based solutions can tremendously accelerate an organisation’s ability to quickly respond to demand, as well as scale to very large levels of user connectivity and traffic encryption – all without undertaking potentially unachievable engineering projects.
Because FortiGate-VM is able to perform at 20Gbps using the AWS C5n.9xlarge instance types, it can support thousands of remote users, regardless of whether they use FortiClient or some other end-user VPN client, looking to securely connecting to a public cloud-based security services hub to access applications that are in the cloud. It also enables them to access on-premise applications through the closest cloud region and on to the private data center using a Direct Connect link to AWS, ultimately providing continuous support for high-speed data transfers from the cloud to datacenters and vice versa.
Ciphers and CPU Affinity: Since in-the-cloud compute is generally bound to general purpose CPUs, its ability to support high-performance crypto negotiations is limited. Choosing the right cipher for the job is an important task, as it will dramatically affect the feasible performance and scale of a secure connectivity solution. We have found that for IKE Phase 2 settings, the best performance can be achieved using chacha20poly1305 ciphers. Furthermore, since encryption and decryption are very CPU-intensive operations, leveraging compute instances with up-to 32 cores enables customers to benefit from increased performance by spreading connectivity across multiple VPN tunnels, each with its own dedicated compute resources for cryptographic operations.
IPSec Aggregates – Some organizations may need to secure high-speed links that require performance higher than that those available on a single virtual network interface of a compute instance used by the FortiGate-VM. FortiGate users can aggregate tunnels to equally spread traffic across four different virtual interfaces as part of a single IPSec tunnel to achieve high throughput for site-to-site encrypted connections. This capability is extremely important for large volume secure communications across clouds and datacenters.
Enable Secure SD-WAN – In order to avoid the undesired effects of a traffic burst on business-critical applications, it is recommended that organisations isolate traffic with very clear SD-WAN SLAs that cannot afford to be disrupted. This can be achieved by splitting traffic across different VPN tunnels (whether aggregate or not). FortiGate-VM SD-WAN policies can be used to allocate and reserve tunnel capacity for certain types of traffic, and dynamically allocate additional resource/tunnels to traffic based on the SD-WAN policy. Organizations can then associate different tunnels with different physical connections and explicitly define which traffic is preferred to run over internet (3 in above illustration) connections vs direct connect links (2 in above illustration).
Leveraging Existing Investments
Addressing new or increased capacity requirements due to increased demand for applications hosted in the cloud as well as SaaS services can seem like a significant challenge. But by leveraging the innovation and capabilities in their existing technology investments, organisations can often address a majority of their requirements without significant additional overhead.
Organisations that have invested in Fortinet Security Fabric-based network security infrastructures that include some or all of the following products – FortiGate appliances and VM’s for the overall network security infrastructure, FortiManager/FortiAnalyzer for single pane of glass management and the free or commercial versions of FortiClient for centrally managed end user VPN connectivity – already have many of the tools they need. They enable them to fine tune their existing configurations and environments to address urgent and increasing needs, while addressing critical business requirements, providing the organisation with the lifeline they need to effectively and securely support their increased remote worker communities.
Learn more about how to maintain business continuity through broad, integrated, and automated Fortinet Teleworker Solutions.
Learn how Fortinet’s dynamic cloud security solutions provide increased visibility and control across cloud infrastructures, enabling secure applications and connectivity from data center to cloud.
Read these customer case studies to see how Cuebiq and Steelcase implement Fortinet’s dynamic cloud security solutions for secure connectivity from data center to the cloud.

