
The Four-Step Journey to Securing the Industrial Network
20th May 2020
Just as the digitisation and increasing connectivity of business processes has enlarged the attack surface of the IT environment, so too has the digitisation and increasing connectivity of industrial processes broadened the attack surface for industrial control networks. Though they share this security risk profile, the operational technology (OT) environment is very different from that of IT. This post looks at the key differences and provides a four-step approach to securing the industrial network.
In industries like utilities, manufacturing, and transportation, the operations side of the business is revenue generating. As a result, up time is critical. While up time is important in IT, inter-dependencies in the OT environment make it challenging to maintain up time while addressing security threats. For example, you can’t simply isolate an endpoint that’s sending anomalous traffic. Because of the inter-dependencies of that endpoint, isolating it can have a cascading effect that brings a critical business process to a grinding halt. Or, worse, human lives may be put at risk. It’s important to understand the context of security events so that they can be addressed while maintaining up time.
With up time requirements in mind, securing the industrial network can feel like an insurmountable challenge. Many industrial organisations don’t have visibility into all of the devices that are on their OT networks, let alone the dependencies among them. Devices have been added over time, often by third-party contractors, and an asset inventory is either non-existent or grossly outdated. Bottom line: organisations lack visibility into the operational technology environment.
To help industrial organisations address these challenges and effectively secure the OT environment, Cisco have put together a four-step journey to securing the industrial network. It’s important to note that while it is called a journey, there is no defined beginning or end. It’s an iterative process that requires continual adjustments. The most important thing is to start wherever you happen to be today.
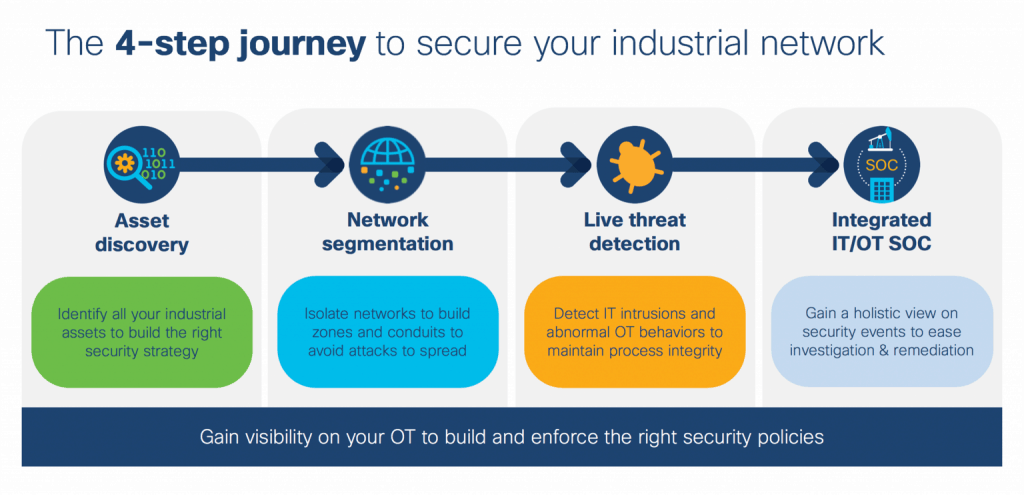
There are many places from which to begin, and what makes a logical first step for one organisation will not necessarily be the same for another. One approach is to start with gaining visibility through asset discovery. By analysing network traffic, deep packet inspection (DPI) can identify the industrial assets connected to your network. With this visibility, you can make an informed decision on the best way to segment the network to limit the spread of an attack.
In addition to identifying assets, DPI identifies which assets are communicating, with whom or what they are communicating, and what they are communicating. With this baseline established, you can detect anomalous behaviour and potential threats that may threaten process integrity. This information can then be fed into a unified security operations centre (SOC), providing complete visibility to the security team.
How you deploy DPI is important. Embedding a DPI-enabled sensor on switches saves hardware costs and physical space, which can be at a premium, depending on the industry. DPI-enabled sensors allow you to inspect traffic without encountering deployment, scalability, bandwidth, or maintenance hurdles. Because switches see all network traffic, embedded sensors can provide the visibility you need to segment the network and detect threats early on. The solution can also integrate with the IT SOC while providing analytical insights into every component of the industrial control system. With DPI-enabled network switches, industrial organisations can more easily move through the four-step journey to securing the industrial network.

